This is how I maintain. It's how I manage stress. For me, it works.
Today I have some important news to cover. The wretched infestation of globalist gremlins we have been dealing with the last few years are busy making their own preparations; to basically wreck everything in sight, so they can feed their greed some more.
POWER, PROFIT AND CONTROL. That's what is important to them, and that’s all they care about. They want it all and are getting ready to take it. Really, it’s a thing they have already done, they just haven't made an official declaration to that effect yet. What I am going to share with you today, among other news stories and opinions I have, is how the robbery will take place - officially.
This plan is NOT just my opinion, oh no, this is THE PLAN.
The Rich Will Get Richer -- Until The Poor Get The Picture.
https://www.zerohedge.com/geopolitical/intentional-destruction-first-covid-now-comes-great-taking
THE GREAT TAKING...THE PLAN TO HAND OVER YOUR ASSETS TO THE BANKSTERS
David Webb is the Author of "The Great Taking". A free download is available here: https://thegreattaking.com/
What is this book about? You should have a look and find out.
It is about the taking of collateral (all of it), the end game of the current globally synchronous debt accumulation super cycle. This scheme is being executed by long-planned, intelligent design, the audacity and scope of which is difficult for the mind to encompass. Included are all financial assets and bank deposits, all stocks and bonds; and hence, all underlying property of all public corporations, including all inventories, plant and equipment, land, mineral deposits, inventions and intellectual property. Privately owned personal and real property financed with any amount of debt will likewise be taken, as will the assets of privately owned businesses which have been financed with debt.
If even partially successful, this will be the greatest conquest and subjugation in world history. Private, closely held control of ALL central banks, and hence all money creation, has allowed a very few people to control all political parties and governments, the intelligence agencies and their myriad front organizations, the armed forces and the police, the major corporations and, of course, the media.
These very few people are the prime movers. Their plans are executed over decades. Their control is opaque. To be clear, it is these very few people, who are hidden from you, who are behind this scheme to confiscate all assets, who are waging a hybrid war against humanity.
David has deep experience with investigation and analysis within challenging and deceptive environments, including the mergers and acquisitions boom of the 80’s, venture investing, and the public financial markets. He managed hedge funds through the period spanning the extremes of the dot-com bubble and bust, producing a gross return of more than 320% while the S&P 500 and the NASDAQ indices had losses. His clients included some of the largest international institutional investors.
I actually had an opportunity to meet David recently, on a conference call that went on for hours. What this man has to say will floor you. This is NOT a drill.
Question:
In the next global financial panic, what are the chances that there will be much of anything remaining in these pools of securities after the secured creditors have helped themselves?
Answer:
There will be a game of musical chairs. When the music stops, you will not have a seat. It is designed to work that way. It is time to ask: cui bono? Who benefits?
It is now assured that in the implosion of “The Everything Bubble”, collateral will be swept up on a vast scale. The plumbing to do this is in place. Legal certainty has been established that the collateral can be taken immediately and without judicial review, by entities described in court documents as “the protected class.” Even sophisticated professional investors, who were assured that their securities are “segregated”, will not be protected.
An enormous amount of sophisticated planning and implementation was sustained over decades with the purpose of subverting property rights in just this way. It began in the United States by amending the Uniform Commercial Code (UCC) in all 50 states. While this required many years of effort, it could be done quietly, without an act of Congress.
These Are The Key Facts:
- Ownership of securities as property has been replaced with a new legal concept of a "security entitlement", which is a contractual claim assuring a very weak position if the account provider becomes insolvent.
- All securities are held in un-segregated pooled form. Securities used as collateral, and those restricted from such use, are held in the same pool.
- All account holders, including those who have prohibited use of their securities as collateral, must, by law, receive only a pro-rata share of residual assets.
- “Re-vindication,” i.e. the taking back of one’s own securities in the event of insolvency, is absolutely prohibited.
- Account providers may legally borrow pooled securities to collateralize proprietary trading and financing.
- "Safe Harbor" assures secured creditors priority claim to pooled securities ahead of account holders.
- The absolute priority claim of secured creditors to pooled client securities has been upheld by the courts. Account providers are legally empowered to “borrow” pooled securities, without restriction. This is called “self help.” As we will see, the objective is to utilize all securities as collateral.
- The “self help” applies to “market participants”, meaning definitely not you, the person whose retirement savings are invested in those markets. “Market participants” is a euphemism for the powerful creditors who control governments via debt. The establish their legal certainty with respect to the financial assets while removing yours. Interestingly, besides a small group of the private mafia behind the veneer of the central banks, nobody else is really protected. Not even the multi-millionaires and billionaires if they hold financial securities in the same collateralized structure..
QUOTE FROM SASHA LATYPOVA:
"From my personal experience, I already lived through one “great taking”, performed by whoever collapsed the Soviet Union. When Ukraine became independent from the former USSR in 1991, the ruble and any savings that anyone had at Sberbank (the only bank that existed in the USSR) disappeared overnight, and were not replaced. One can argue this was a very simple exercise given that only one state-owned bank was involved or needed to implement this reset, and there were no financial instruments, only cash savings in that bank. My grandparents had meager savings there and ended up with zero. I had no money at all as a young person, and I guess that can be a plus - when you own nothing, nobody can confiscate it from you. Afterwards, there was no currency in circulation in the country for approximately 2 years until hryvna was designed and printed and introduced. During those years, people (including me) received paychecks in the form of this - gov issued IOUs exchangeable for goods in stores that had any goods."
MEET THE BANKING CARTEL THAT IS PLANTING THE SEEDS FOR THE NEXT BANKING PANIC AND BAILOUT
https://wallstreetonparade.com/2023/09/meet-the-banking-cartel-that-is-planting-the-seeds-for-the-next-banking-panic-and-bailout/
EXPERTS ON CENTRAL BANK PLANS TO TOKENIZE AND CONFISCATE ALL YOUR PROPERTY
https://www.bitchute.com/video/zp83SuWr3jxE/
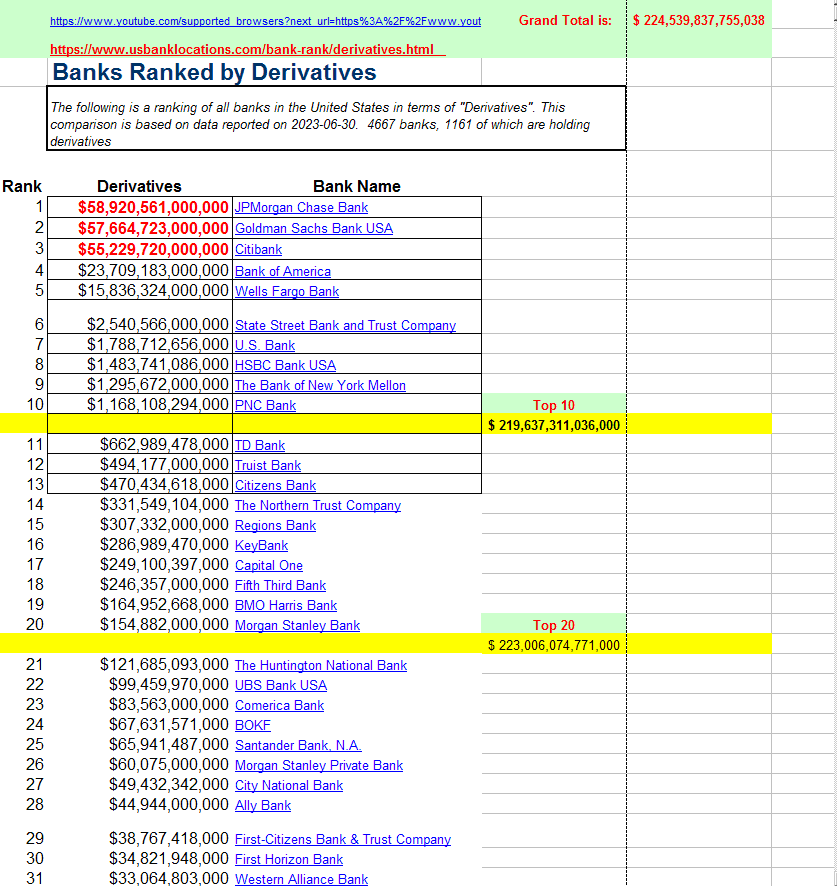
US BANKS RANKED BY DERIVATIVES EXPOSURE
https://www.usbanklocations.com/bank-rank/derivatives.html
A derivative is basically a loan, but it differs from the type of loan you are probably familiar with in one very important way. Loans are debt. Debt is a liability. Too much debt is a weakness, financially. But a derivative is not reported on financial statements as a liability. Derivatives are "legally" (clearly not lawfully) reported as assets.
Derivatives exposure is financial weakness, but due to some very deceptive accounting practices that have been legalized by those who benefit from this, derivative exposure is reported as financial strength. Borrowed money looks like liquid cash on hand on a typical set of corporate financial statements. When people looking for good investments choose where to invest they look for strong companies, but today they cannot find any.
Why would any company use derivatives? Well, a smart one would not, but those that have do so because the money is cheap and easy to obtain. When companies borrow funds they do what you would do, they look for the best rates and terms they can qualify for, but a derivative option can look more attractive simply because it gives them access to large sums at rates and terms they DO NOT qualify for. It's a risky move that could either pay off big or bite them in the ass, and these messed up accounting rules allow them to do this in secret. Nobody has to know they took such a risk. It's like going to a loan shark, but they are called sharks for a reason.
All kinds of large companies, including banks, securities firms, brokerage houses, etc. all APPEAR to be solid, but they are not. If their loans are called, meaning they are asked to pay, or if the repayment terms of these massive loans cannot be met, those borrowers, along with all their investors, will go POOF!
And this situation is like a string of dominoes. All it takes is one big borrower to fuck up somehow, and everything downstream of them collapses. Now if I had to speculate on which one of the criminal institutions listed in the chart above is most likely to be either deliberately sacrificed or thrown under the bus to kick this off my guess is that it will be the Bank of America. It's not the largest, but it is large, and in a previous post I mentioned a strange situation that was reported on in Wall Street on Parade not too long ago, in which BofA had apparently prepared for its own impending bankruptcy by setting up numerous financially empty shell companies to take the heat of creditors as well as bankruptcy filing paperwork, but this paperwork has to date not been filed.
Is this "legal"? Probably not. But then "legal" is a relative term that has very little to do with ethics. I don't have much of anything to protect, but if I did, and any part of that involved BofA, I would remedy that situation fast. But in all honesty, it does not matter where your personal exposure is. If you have any at all you are vulnerable to a total loss of whatever that is. The best possible position to be in right now is debt-free, in possession of some tangible asset of value, and an ability to provide some kind of skilled labor that will be in demand later should everything go tits up.
The way things in general look to me, all things considered, is there is a timetable in motion here, and every shit move on the globalist agenda has an appointment slot. I cannot really see this economic time bomb ticking away too much longer. My gut is telling me it will most likely go off sometime next year, so by this time next year, we will all be deep in "the suck".
Something Positive:
MY BUDDY TODD CALLENDER TAKES THE DEPOP AGENDA TO THE SUPREME COURT!
https://rumble.com/v40o4ni-todd-callender.html
This outcome should be interesting to watch. This is a real court case that will formally accuse those responsible for trying to force poisonous vaccinations of Americans.
Todd and I first met way back when he was doing work for America's Frontline Doctors. Todd rightfully bailed on that group when it became clear that Simone Gold was in the market for a gold toilet seat. Since then we have been in contact somewhat regularly. I did a few alt media shows with him, appearing to discuss various things like the real power handling capacity of large cell masts and other pandemic related news.
This announcement, that he has a case officially docketed on the Supreme Courts 2024 calendar is a big deal. It has been suggested, rather astutely I might add, that his case was selected as a setup, to give the kind of predetermined decision we might expect, since the government is not in the habit of incriminating itself, but the fact his case was selected to be heard at all is, I think, a major victory.
What this essentially means is the judicial branch of government has just legitimized these claims. Its no longer a "conspiracy theory". And this is something I predicted a long time ago, that at some point we would turn a corner with regard to someone officially acknowledging what actually motivated this massive, global scam I call the corona-hoax.
I think when this case goes to trial next year the publicity that it generates will be a game changer, if of course, everyone does their part to flood the media with stories about it, to focus attention on the case itself. Regardless of the outcome, this is sure to be a lighting rod for similar accusations.
As I have said before, if you want things to change you have to stop asking questions and start making accusations. Todd is leading the way, so my advice is to get behind him.
Understanding the Creepy Pseudoscience and Religion Behind Eugenics
For those unfamiliar with eugenics, it is a pseudoscience whose thesis is that it is possible to improve the “breeding stock” of humanity (positive eugenics) by ensuring that, for example, the Nazi ideal of pure-blood Aryan Germans breeding with other pure-blood Aryan Germans will create blond-hair, blue-eyed “Übermensch” or “Supermen”.
The darker side is called negative eugenics: the poisonous idea that society can be improved by sterilizing, aborting, euthanizing or even murdering those deemed unfit or “useless eaters”.
Many of the largest fortunes the world has ever seen were left to foundations that continue the work of eugenics today.
https://dailynewsfromaolf.substack.com/p/censored-the-study-that-shows-a-staggering
"A groundbreaking study [17 Countries, 4 Continents ] found that 17 million people died worldwide after the Covid “vaccine” rollout and therefore should be garnering worldwide attention and calls for an immediate cessation of all Covid vaccines. Instead, it has been CENSORED!
The shocking study, COVID-19 vaccine-associated mortality in the Southern Hemisphere, by Drs. Denis Rancourt, Marine Baudin, Joseph Hickey and Jérémie Mercier was published September 17, 2023, yet, also shockingly the study has not had the attention it deserves, but, has met only censorship and narrative-confirming “fact-checks” on the safety and effectiveness of the as-yet untested Covid-19 “vaccines.”
The team of doctors studied 17 countries across 4 continents, in Latin America and in the equatorial region which provided them with a representative sample of the world. “We calculate the toxicity of the vaccine for all ages,” explained Dr. Rancourt, “given the number of doses given worldwide to conclude that 17 million people would have been killed by this vaccine.”
ANALYSING BATCH IDS OF THE PFIZER SHOTS, HOW MANY PEOPLE DIED
https://www.bitchute.com/video/828LP0kemJUz/?list=subscriptions
Vaccinator fails pegged. As it turns out, certain jabbers were much better assassins than others.
DR. LEE MERRITT AND I FINALLY MEET!
https://rumble.com/v3zhihw-dr-lee-merritt-md.html
This is a replay of a recent MD4CE conference call which had Dr. Lee Merritt as the guest presenter. These meetings are sponsored by Dr. Stephan Frost and moderated by Charles Kovess. I am a regular participant and contributor in this group and attend their twice weekly standing calls. The core contributors usually come on a bit early, before the replay recording begins, so we had an opportunity to have a quick exchange, at the start of which another doctor, Daria Schooner MD, interrupted to basically explain to Dr. Merritt who I was, since she didn't know, and she explained how important she felt my work is. Daria graciously described me as the biggest contributor to this group over the past year. So that was unexpected, and just great, because that introduction gave me the street cred I needed to really get Lee's attention.
Hearing that, Lee asked me for my contact info and promised a personal call soon. Lee has a lot of knowledge, high security clearance type stuff and work experience in advanced bioweaponry. She is aware of the bio cyber area but a little sheepish about covering it. And this is the hell hole I am digging into, so I was gunning for an offline chat with her and she promised me one, so mission accomplished.
You probably won't see a public interview between the two of us unless she wants to interview me for her channel or something to muse over some less dangerous topics. I want to talk with her about some of the documentation I am not supposed to have, and slipped her one of those papers on this call to review. She dances around some of these areas publicly, but she knows more, and I want to know what that is, so this meet up is going to be the two of use sharing info and playing the connect the dots game at a level you cannot do on camera.
The thing about Lee is, for the last three years I would conclude something extraordinary on my own and a week later I would Lee say the exact same thing on some show. And I told her that. I told her it made me think to myself, "What the hell?" Does Lee Merritt actually poach my blog?" And that made her laugh, which was fun. It was uncanny how many times this happened. I was always about 6-8 months ahead on insider stuff and she usually was about 4. Just by comparing the dates of certain articles I posted from 2020-2022 with her appearances during the same time proves it.
People don’t generally believe me because, let's face it, I am me, but they do respect Lee, and hearing her later come to the same conclusions I was arriving at was so encouraging, and also like having my own PhD carrier pigeon. Lee single-handedly kept me at my desk month after month early on. Today I have so many things that compliment and confirm things she muses about that I know she has not seen yet. The two of us comparing notes is going to be epic. Not sure when this will happen just yet but it will, and I can't wait. I have a whole file just on her at home.
I only heard her say one thing on this call that I would challenge, and that was the stuff about instant flu spread having a historical basis. I'm not buying that, because of where it came from. Blavatsky, Steiner, et.al all these people, and there were 5-6 of them, were parapsychological gurus in their day and they all ran what amounted to fortune teller circuits, spirit cults and enlightenment mystery schools. They all had a huge influence on people in general, but look into any of them hard and it's clear they had had backdoor relationships to power like Nixon/Dixon and Reagan/Barron. We are gonna have to hash that one out. I think offering such weak evidence creates doubt where it should not be, and that whole theory she floats out is one I can shoot a dozen holes in without much effort. I don't mean to be a censor to anyone, least of all her, but coming from her that sort of acknowledgement is the inch the enemy needs to take several miles of our territory.
There are other things she could include in this presentation that take back territory from them, like JJ Couey's observations as to why the virus/no virus crowds argument only looks strong. It's not, not at all. Yeah, it makes sense that if viruses can be disproven a lot of what follows from virology can be debunked, but they do not offer a replacement theory, and there is one, hell, I have offer a great one in my second book you will never hear elsewhere. Simply maintaining there are no viruses and letting that be your entire position ignores a whole lot of evidence that will never go away. This evidence is of course all the result of faulty observations, flawed logic, and outright fraud that is misleadingly presented and maliciously used to deceive laypeople, but it is there, and they just ignore that. Its presence is as serious a problem as believing in fake viruses, that is just as important to expunge from lexicon of professional medicine as dispelling the superstition. Leaving it there unaddressed has allowed this con to be repeated every couple generations for the last couple THOUSAND years!
These people come to the debate table stating they don't have a better explanation for all of that, which is lazy as hell, stubbornly hiding behind this weak defense that they are only there to refute the current understanding, but that’s a half-ass job. If they win it means what the want is for everyone to just dismiss and throw out "all things virology" and revert back to the previous understanding which, by the way, was demons! No shit. Before Pasteur, another con man, showed up on the scene if you got terminally ill, what you needed was an exorcist.
The "no virus" people, a movement spearheaded by people like Tom Cowen and Andrew Kauffman, don't realize that is actually the position they are defending. And that is why, despite all the good they do, they get lumped into the controlled opposition bin with more serious decepticons like Peter McCullough and Robert Malone. And JJ Couey gave a perfect explanation for their strange behavior in a clip excerpt I put at the bottom of a recent post: http://estateartistry.com/blog/brain-science-the-mind-is-useless-if-the-eyes-are-blind
So definitely watch that.
More Libtard Politics and War Mongering
https://www.bitchute.com/video/jbSSY1D0H89M/
This is so ridiculous. "Congestion is costing NYC businesses 20 billion annually?" Oh fuck off, you daft cunt! You don't just float that out like a fact. Based on what? Prove it! When the hell has a business ever moaned about high traffic? Hell, they pay premium prices for high traffic locations.
You know what really costs them money? NO TRAFFIC! Fuckin morons. Hang em high.
I have a great answer to this bullshit. Remove the plates on your car. If everyone simply does that they are fucked.
NEW YORK PASSES THE BILL ALLOWING THEM TO KIDNAP AND IMPRISON NY RESIDENTS SUSPECTED OF HAVING "COVID" AGAINST THEIR WILL !!!
https://govt.westlaw.com/nycrr/Document/I3783ab18c22411dd80c2c6f42ff0193c?viewType=FullText&originationContext=documenttoc&transitionType=CategoryPageItem&contextData=%28sc.Default%29
Yeah. You heard right. If you live in New York you better get the hell out right now. I swear this is a bridge too far.
DO YOUR PART FOR GLOBAL WARMING: STOP BREATHING!
https://www.zerohedge.com/political/do-your-part-global-warming-stop-breathing
Ha! Finally... A WEF measure I can get behind. Attention, all you fools who have been impersonating speed bumps to save the planet: Here's the ultimate virtue signal. Go wave this flag. I promise I will notice you this time.
TENNESSEE SLAPS BLACKROCK WITH FIRST-OF-ITS-KIND CONSUMER PROTECTION LAWSUIT OVER ESG SHAM
https://www.zerohedge.com/markets/tennessee-slaps-blackrock-first-its-kind-consumer-protection-lawsuit-over-esg-sham
I covered ESG in previous posts. This has been how the WEF has managed to reward corporate support of its absurdly destructive climate change policies. Either you endorse and promote that shit or they will tax your non-compliance with carbon footprint type invoices.
Where this sham begins to impact investors is when companies adopt ineffectual "green" policies that involve equipment and practices that are hugely expensive, and as a result become financially dependant upon subsidies offered by the gov't that are UN-sustainable. Being a climate change whore eventually impacts their bottom line, which is where investors end up holding the bag, and this sort of back-door dealing has finally been exposed for what it is.
JOURNALIST WHITNEY WEBB EXPOSES THE WEF FALSE FLAG PLAN TO CARRY OUT A MASSIVE CYBER ATTACK IN 2024 THAT WILL PAVE THE WAVE FOR A REGIONAL WAR IN THE MIDDLE EAST.
https://dailynewsfromaolf.substack.com/p/shes-exposing-the-wef-false-flag/comments
https://www.youtube.com/watch?v=Y36ZEKYMvzM
When it comes to geopolitical mudslinging, I find it endlessly entertaining that the same people who have pursued the declared goal of "Total Information Awareness" all the way to the point of it becoming a reality, constantly float out such outrageous accusations with such thin evidence.
These are the same clowns that are always being caught off guard by whatever sort of attack succeeds, after which we are treated to a Broadway show quality level of shame and lament over some gaping hole of a blind spot they somehow had, which provides an equally lame excuse that then seamlessly morphs into closure that neatly zips up a story that always ends the same way;
Where they generously grant themselves "self-forgiveness", for being conveniently asleep at the switch.
At some point, any reasonable person can only conclude that the entire foundational premise of "National Security and Defense vs. Invisible Enemy" is a total farce in which both sides of any conflict consist of colluding members on the same deep state committee.
THE U.S. STANDS ALONE IN THE WORLD SUPPORTING GENOCIDE AGAINST THE PALESTINIAN PEOPLE
https://vaccineimpact.com/2023/the-u-s-stands-alone-in-the-world-supporting-genocide-against-the-palestinian-people/
This article is pretty long, but one of the things you will learn if you read it, is all of the reasons the US has for supporting this atrocious genocide. Are the good reasons? Not really. In fact, it's worse than you ever thought.
FULL SCALE NAVAL WAR BREAKS OUT IN RED SEA AND (PROBABLY FAKE OR FALSE FLAG) "CYBER ATTACKS"
https://vaccineimpact.com/2023/full-scale-naval-war-breaks-out-in-red-sea-as-cyber-attacks-take-down-fuel-station-distribution-in-iran/
Add Taiwanese container shipping line Evergreen and Belgian tanker owner Euronav to the growing list of major shipping firms halting all sails through the Red Sea strait. This brings the total to seven.
Also, the UK Navy disclosed more details regarding today’s incident in the Red Sea, reporting that an explosion hit the side of a commercial vessel near Yemen. The Norwegian owner of the ship confirmed that an “unidentified object” had impacted the vessel on the port side.
12/19/23 Bloomberg reports:
YEMEN HOUTHIS SAY THEY ATTACKEDMSC CLARA CONTAINER SHIP
YEMEN HOUTHIS CLAIM THEY ALSO ATTACKED SWAN ATLANTIC OIL TANKER
Between 10% and 12% of global trade passes through the Red Sea each year.
US EARNS THE HATE WITH THINLY VEILED MOTIVES
https://www.zerohedge.com/geopolitical/houthis-vow-keep-attacks-us-unveils-details-multi-national-naval-force
https://www.zerohedge.com/markets/red-sea-blockage-means-new-round-surging-cost-push-inflation
So we're not defending Israel, we are "protecting" free trade? Is anyone buying this charade?
https://expose-news.com/2023/11/19/a-message-from-reiner-fuellmich/?cmid=3cdb44fa-eb81-4d42-adc9-2cf88935dba6
"As has been reported in the Expose, attorney Dr. Reiner Fuëllmich was arrested on Friday the 13th October while trying to renew a passport. He was detained in Mexico and escorted back to Germany where he was rearrested and imprisoned. There has been very little publicity surrounding his arrest and current situation, however, we have previously published an update on Dr. Fuëllmich that had been shared by his friend Dr. Elsa Schieder and attorney Dagmar Schoen on the 28th October."
IS YOUR STATE SUPPRESSING YOUR GUN RIGHTS? TRY STARTING A MILITIA
https://www.youtube.com/watch?v=dCSF8mZy80M
Washington Gun Law President, William Kirk, heads out to Holton Township in Michigan, who not only declared themselves a Second Amendment Sanctuary, but also have formed the town's first militia. This move, which goes far beyond the normal declaration and instead implements a militia which anyone who is lawfully permitted to carry a firearm may join.
So learn why they did this, why others may want to think about it, and why some will never be able to do this, and arm yourself with education today.
You Vill Eat Zee Bugs…
https://live.childrenshealthdefense.org/chd-tv/shows/financial-rebellion-with-catherine-austin-fitts/pharma-food-biotech-on-your-plate-with-elze-van-hamelen-fr/
Believe it or not, I actually know Elze Van Hamlin. She and I spoke quite often after my first book was published and she wrote a fabulous two page spread on it that appeared in Gezond Verstand in November of 2019. The magazine was in Dutch but it has a fairly large circulation that extended all the way to South Africa, so Elze almost single handedly delivered me a global audience with that review. (after which it was promptly censored globally)
Anyway, she is quite the researcher herself and pretty well known in Europe. In this clip she is being interviewed by Catherine Austin Fitts, who did a deep dive into this toxic sludge and compiling all the supporting research at Solari for this expose Elze is doing on what this shit actually is, and I gotta say, it's quite a bit more than I knew about it. I knew enough to know I should not go near it, but after hearing this, to say these products are simply nasty and toxic is a gross understatement. You should hear this.
To me, knowing what I know about vaccines, vaccine production, and vaccine history, it sounds a lot like these products are literally oral vaccine formulations. The lack of health and safety oversight, the flawed production processes, the ridiculous amount of money being thrown at developing a thing that has no market whatsoever reveals almost as much about the real purpose behind this stuff as the ingredients that go into it.
I see them doing the same thing with these Franken foods as they did with deadly vaccines, where they made up the term "medical countermeasures", to hide the fact that they were never intended to be any sort of medicinal product. The vaccines were always biological depopulation bioweapons meant to murder people in hideous ways. Funding and pushing synthetic foods is the same play, different day. The environment in which this work advances is literally a wild west in terms of any real checks against the levels of sinister that are possible. Just like the vaccines, nobody is legally responsible for anything connected to this agenda.
Someone out there might want to put some of this shit under the scope to see what it looks like. I am tempted to do the same but like the vaccine solutions, which I would advise against even coming into physical contact with, I frankly don't even want to handle it. It is basically bovine (but I suspect also probably human) fetal matter, cancerous tissue and chemical poisons, created with a process that can only breed and harbor rapidly proliferating bacterial pathogens.
Remember all the stories about unclean Pfizer production facilities that were shipping out vaccines by the barrel? Same deal. Lab grown meat is straight-up carrion, soaked in a bath of artificial flavorings, and I guarantee the plan they have is to label this as "organic" to sneak some version of it into everything like they poisoned everything medicinal with graphene.
Yikes. This is beyond repulsive. Branded as such or not, I think I have eaten my last fast food menu item, and damn close to passing on anything I don't slaughter myself. Seriously, man, I'd rather trap and fry squirrels than take a chance at the supermarket right now.
FDA APPROVED, CONTROVERSIAL LAB-GROWN MEAT BECOMES A REALITY
https://www.zerohedge.com/commodities/fda-approved-controversial-lab-grown-meat-becomes-reality
"FDA Approved" has a new meaning you all better become aware of and take seriously.
It means "Poisonous, Unsafe, Not for Human Consumption, or Use"
"In 2025, the nuggets segment is expected to account for the largest share of the lab-grown meat market,"
Ya hear that? Pay attention. NO MORE NUGGETS FOLKS!
This Will Probably Be My Last Blog Post For The Year.
On a recent call we heard from an attorney who was doing some important case work, and he finished up quick. We ended the call on time, but about 15 people still wanted to discuss other topics. Charles Kovess had to scram, so he gave me host privileges and the remaining participants began asking me questions about synthetic biology.
THREE HOURS LATER…
Everyone was so gob smacked Stephan Frost insisted I give a formal presentation for MD4CE in January to the usual room of 80+ participants (which is stacked with at least 40 PhD's. from every field). The exact date is not set because I told him this is going to take a LOT of work to create. I am working feverishly on this now. This will hopefully clear a lot of people up as to what's really going on, but a 90 minute presentation on this material is a massive project. (Probably 60 pages of script, a huge slide deck with diagrams and video clips, source appendix, etc…) No xmas break for me, that’s for sure, but I did manage to obtain a dedicated research assistant in AU, thankfully, to help with the visual aids.
The topic will be Nanotechnology, and the Tools of Electronic Biological Warfare. This will cover bio-photonics, optogenetics, teslaphoresis, synthetic biology, and the Bio-API material I have been covering here in a series of articles. Despite there being a bunch of people out there all talking about this stuff I seem to be the only one I can find that is able to lay it all out in the proper context, and that needs to be done.
Preparing for this lecture will unfortunately take precedence over penning blog articles, so I apologize to my regular readers for that. I will continue to follow certain developments however, and if something really important pops up I will give it a mention, but until this project is finished I am gong to have to devote a lot of attention to it.
When a final date is set I will announce it here, and for anyone not on the invite list, a replay will appear on Charles Kovess's Rumble channel 48 hours after.
Thanks for stopping by.
I wish everyone a Merry Christmas and I will see you again in the New Year.
In the meantime; DO NOT COMPLY!
-John



 RSS Feed
RSS Feed